Scientists at Fermilab in the U.S. have demonstrated, for the first time, sustained and long-distance teleportation of qubits of photons with fidelity greater than 90%.

New research, published in Nature, has measured highly sought-after Majorana quantum states. A team of theoretical and experimental physicists have designed a new ultra-thin material that they have used to create elusive quantum states. Called one-dimensional Majorana zero energy modes, these quantum states could have a huge impact for quantum computing.
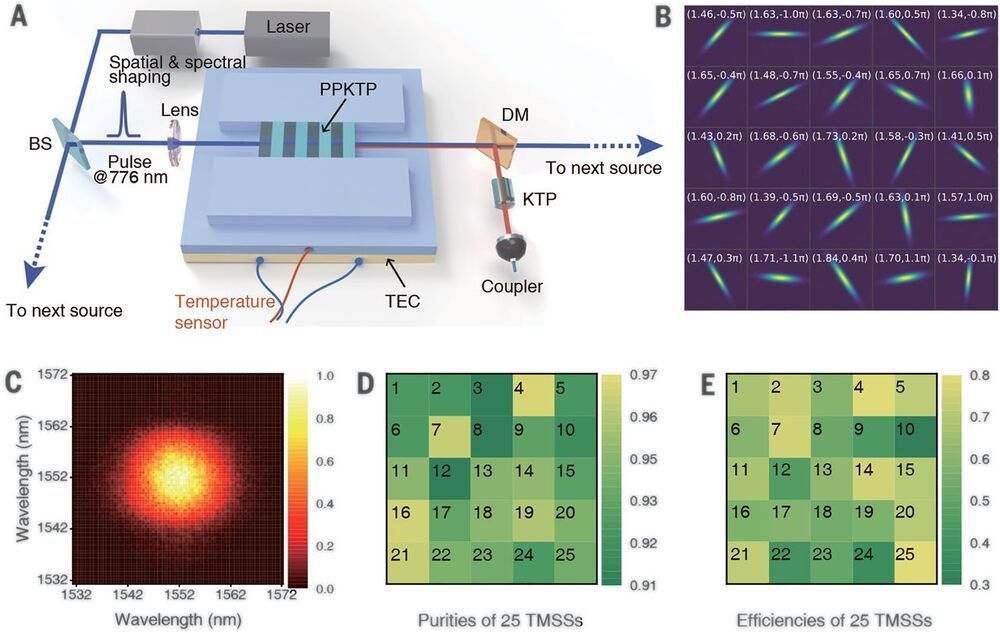
Quantum computational advantage or supremacy is a long-anticipated milestone toward practical quantum computers. Recent work claimed to have reached this point, but subsequent work managed to speed up the classical simulation and pointed toward a sample size–dependent loophole. Quantum computational advantage, rather than being a one-shot experimental proof, will be the result of a long-term competition between quantum devices and classical simulation. Zhong et al. sent 50 indistinguishable single-mode squeezed states into a 100-mode ultralow-loss interferometer and sampled the output using 100 high-efficiency single-photon detectors. By obtaining up to 76-photon coincidence, yielding a state space dimension of about 1030, they measured a sampling rate that is about 1014-fold faster than using state-of-the-art classical simulation strategies and supercomputers.
Science, this issue p. 1460
Quantum computers promise to perform certain tasks that are believed to be intractable to classical computers. Boson sampling is such a task and is considered a strong candidate to demonstrate the quantum computational advantage. We performed Gaussian boson sampling by sending 50 indistinguishable single-mode squeezed states into a 100-mode ultralow-loss interferometer with full connectivity and random matrix—the whole optical setup is phase-locked—and sampling the output using 100 high-efficiency single-photon detectors. The obtained samples were validated against plausible hypotheses exploiting thermal states, distinguishable photons, and uniform distribution. The photonic quantum computer, Jiuzhang, generates up to 76 output photon clicks, which yields an output state-space dimension of 1030 and a sampling rate that is faster than using the state-of-the-art simulation strategy and supercomputers by a factor of ~1014.

On December 3, Science magazine published a scientific paper by Chinese scientists on the results of experiments with a prototype quantum computer.
It was widely reported in the media that the Chinese system needed only 200 seconds to carry out a computation that would take over two billion years using the fastest supercomputer existing today.
The experiments were designed and carried out by a top-level research group led by Pan Jianwei and Lu Chaoyang of the University of Science and Technology in Hefei, China. Pan is one of the most famous Chinese physicists today, referred to once in Nature magazine as the “Father of the Quantum.”
Quantum key distribution is one kind of important cryptographic protocols based on quantum mechanics, in which any outside eavesdropper attempting to obtain the secret key shared by two users will be detected. The successful detection comes from Heisenberg’s uncertainty principle: the measurement of a quantum system, which is required to obtain information of that system, will generally disturb it. The disturbances provide two users with the information that there exists an outside eavesdropper, and they can therefore abort the communication. Nowadays, most people need to share some of their private information for certain services such as products recommendation for online shopping and collaborations between two companies depending on their comm interests. Private Set Intersection Cardinality (PSI-CA) and Private Set Union Cardinality (PSU-CA), which are two primitives in cryptography, involve two or more users who intend to obtain the cardinalities of the intersection and the union of their private sets through the minimum information disclosure of their sets1,2,3.
The definition of Private Set Intersection (PSI), also called Private Matching (PM), was proposed by Freedman4. They employed balanced hashing and homomorphic encryption to design two PSI protocols and also investigated some variants of PSI. In 2012, Cristofaro et al.1 developed several PSI-CA and PSU-CA protocols with linear computation and communication complexity based on the Diffie-Hellman key exchange which blinds the private information. Their protocols were the most efficient compared with the previous classical related ones. There are also other classical PSI-CA or PSU-CA protocols5,6,7,8. Nevertheless, the security of these protocols relies on the unproven difficulty assumptions, such as discrete logarithm, factoring, and quadratic residues assumptions, which will be insecure when quantum computers are available9,10,11.
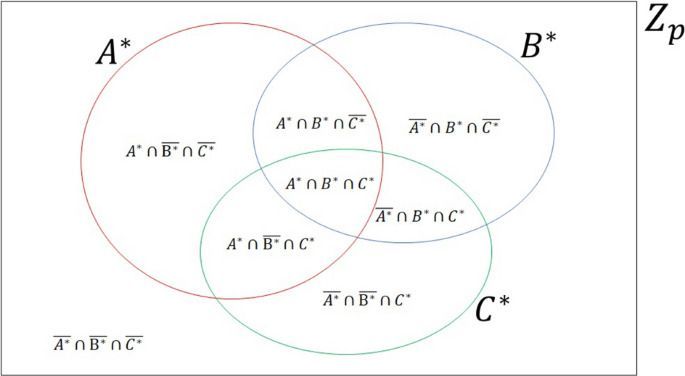
For the sake of improving the security of PSI-CA protocols for two parties, Shi et al.3 designed a probabilistic protocol where multi-qubit entangled states, complicated oracle operators, and measurements in high N-dimensional Hilbert space were utilized. And the same method in Ref.3 was later used to develop a PSI-CA protocol for multiple parties12. For easy implementation of a protocol, Shi et al.13 leveraged Bell states to construct another protocol for PSI-CA and PSU-CA problems that was more practical than that in Ref.3. In both protocols Ref.3 and Ref.13, only two parties who intend to get the cardinalities of the intersection and the union of their private sets are involved. Although Ref.12 works for multiple parties, it only solves the PSI-CA problem and requires multi-qubit entangled states, complicated oracle operators, and measurements. It then interests us that how we could design a more practical protocol for multiple parties to simultaneously solve PSI-CA and PSU-CA problems. Inspired by Shi et al.’s work, we are thus trying to design a three-party protocol to solve PSI-CA and PSU-CA problems, where every two and three parties can obtain the cardinalities of the intersection and the union of their respective private sets with the aid of a semi-honest third party (TP). TP is semi-honest means that he loyally executes the protocol, makes a note of all the intermediate results, and might desire to take other parties’ private information, but he cannot collude with dishonest parties. We then give a detailed analysis of the presented protocol’s security. Besides, the influence of six typical kinds of Markovian noise on our protocol is also analyzed.

Super-fast quantum computers and communication devices could revolutionize countless aspects of our lives—but first, researchers need a fast, efficient source of the entangled pairs of photons such systems use to transmit and manipulate information. Researchers at Stevens Institute of Technology have done just that, not only creating a chip-based photon source 100 times more efficient that previously possible, but bringing massive quantum device integration within reach.
“It’s long been suspected that this was possible in theory, but we’re the first to show it in practice,” said Yuping Huang, Gallagher associate professor of physics and director of the Center for Quantum Science and Engineering.
To create photon pairs, researchers trap light in carefully sculpted nanoscale microcavities; as light circulates in the cavity, its photons resonate and split into entangled pairs. But there’s a catch: at present, such systems are extremely inefficient, requiring a torrent of incoming laser light comprising hundreds of millions of photons before a single entangled photon pair will grudgingly drip out at the other end.
University of Copenhagen researchers have advanced their quantum technology to such a degree that classical computing technology can no longer keep up. They have developed a chip that, with financial backing, could be scaled up and used to build the quantum simulator of the future. Their results are now published in Science Advances.
First came Google. Now, researchers at the University of Copenhagen’s Niels Bohr Institute in collaboration with University of Bochum have joined Google in the race to build the world’s first quantum computer with what they are calling a “major breakthrough.”
“We now possess the tool that makes it possible to build a quantum simulator that can outperform a classical computer. This is a major breakthrough and the first step into uncharted territory in the world of quantum physics,” asserts Professor Peter Lodahl, Director of the Center for Hybrid Quantum Networks (Hy-Q).

The first step is to understand qubits and superposition. The next one is to get a handle on the business advantage that this technology represents.
If “figure out quantum computing” is still in your future file, it’s time to update your timeline. The industry is nearing the end of the early adopter phase, according to one expert, and the time is now to get up to speed.
Denise Ruffner, the vice president of business development at IonQ, said that quantum computing is evolving much faster than many people realize.

JILA physicists have boosted the signal power of their atomic “tweezer clock” and measured its performance in part for the first time, demonstrating high stability close to the best of the latest generation of atomic clocks.
The unusual clock, which uses laser tweezers to trap, control and isolate atoms, offers unique possibilities for enhancing clock performance using the tricks of quantum physics as well as future applications in quantum information processing, quantum simulation, and measurement science.
Described in a Nature paper published online Dec. 16, the clock platform is a rectangular grid of about 150 strontium atoms confined individually by optical tweezers, which are created by a laser beam aimed through a microscope and deflected into 320 spots. This upgraded version of the clock has up to 30 times as many atoms as the preliminary design unveiled last year, due mainly to the use of several different lasers, including a green one for trapping the atoms and two red ones to make them “tick.”
A joint team of researchers at Fermilab and partner institutions have achieved quantum teleportation, teleporting information over a distance of 44 kilometers. The remarkable achievement supports the premise that scientists and engineers can build a workable and high-fidelity quantum network using practical devices.