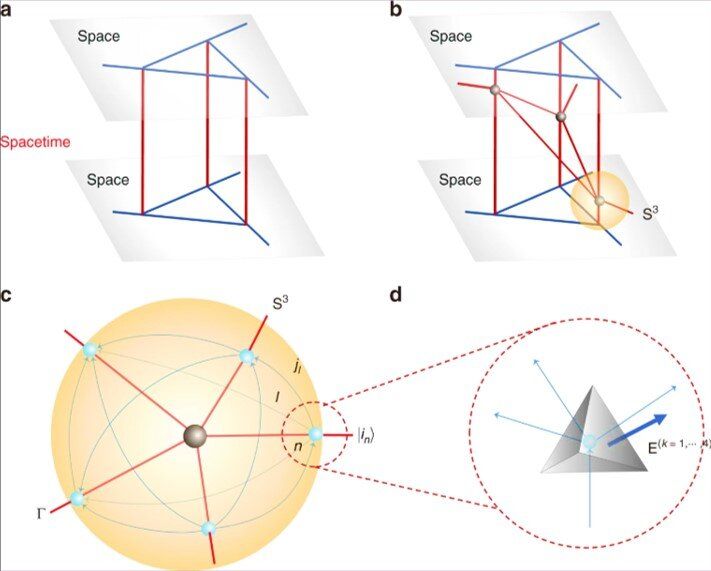
Quantum simulation plays an irreplaceable role in diverse fields, beyond the scope of classical computers. In a recent study, Keren Li and an interdisciplinary research team at the Center for Quantum Computing, Quantum Science and Engineering and the Department of Physics and Astronomy in China, U.S. Germany and Canada. Experimentally simulated spin-network states by simulating quantum spacetime tetrahedra on a four-qubit nuclear magnetic resonance (NMR) quantum simulator. The experimental fidelity was above 95 percent. The research team used the quantum tetrahedra prepared by nuclear magnetic resonance to simulate a two-dimensional (2-D) spinfoam vertex (model) amplitude, and display local dynamics of quantum spacetime. Li et al. measured the geometric properties of the corresponding quantum tetrahedra to simulate their interactions. The experimental work is an initial attempt and a basic module to represent the Feynman diagram vertex in the spinfoam formulation, to study loop quantum gravity (LQG) using quantum information processing. The results are now available on Communication Physics.
Classical computers cannot study large quantum systems despite successful simulations of a variety of physical systems. The systematic constraints of classical computers occurred when the linear growth of quantum system sizes corresponded to the exponential growth of the Hilbert Space, a mathematical foundation of quantum mechanics. Quantum physicists aim to overcome the issue using quantum computers that process information intrinsically or quantum-mechanically to outperform their classical counterparts exponentially. In 1982, Physicist Richard Feynman defined quantum computers as quantum systems that can be controlled to mimic or simulate the behaviour or properties of relatively less accessible quantum systems.
In the present work, Li et al. used nuclear magnetic resonance (NMR) with a high controllable performance on the quantum system to develop simulation methods. The strategy facilitated the presentation of quantum geometries of space and spacetime based on the analogies between nuclear spin states in NMR samples and spin-network states in quantum gravity. Quantum gravity aims to unite the Einstein gravity with quantum mechanics to expand our understanding of gravity to the Planck scale (1.22 x 1019 GeV). At the Planck scale (magnitudes of space, time and energy) Einstein gravity and the continuum of spacetime breakdown can be replaced via quantum spacetime. Research approaches toward understanding quantum spacetimes are presently rooted in spin networks (a graph of lines and nodes to represent the quantum state of space at a certain point in time), which are an important, non-perturbative framework of quantum gravity.