The malware now attempts to disable Microsoft antivirus protection.


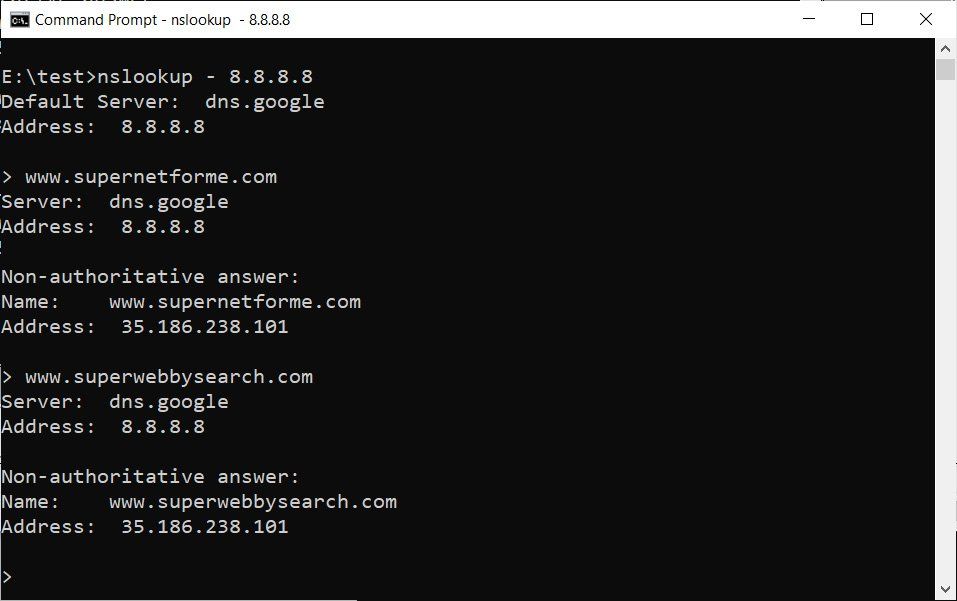
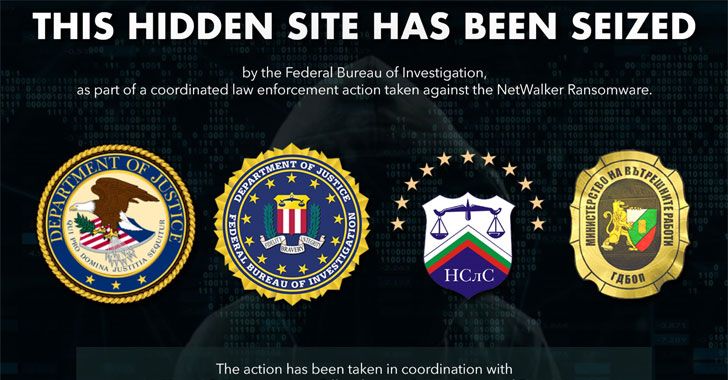

Law enforcement agencies dismantled the infrastructure of Emotet, a notorious email-based Windows malware behind several botnet-driven spam campaigns.
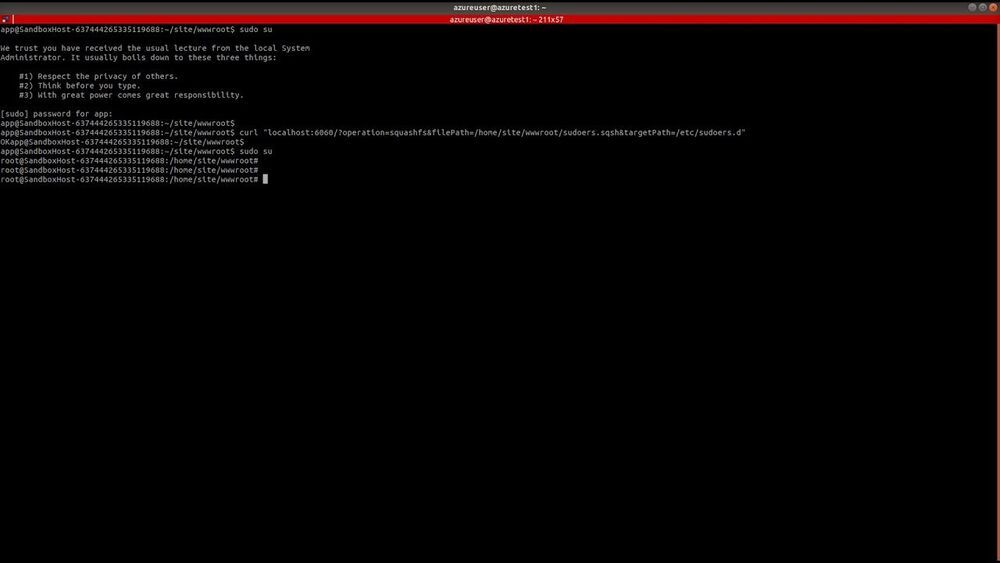
Researchers detail docker container escape bug affecting microsoft azure functions.

Well, maybe they would be good memories. 😃
Quantum computers, according to experts, will one day be capable of performing incredible calculations and nearly unfathomable feats of logic. In the near future, we know they’ll help us discover new drugs to fight disease and new materials to build with. But the far future potential for these enigmatic machines is as vast as the universe itself.
The realm of classic science fiction is littered with ideas that today’s experts believe lie within the realm of reality – if not today’s reality, then perhaps tomorrow’s quantum computer-laden one. One of those ideas comes straight out of a Paul Verhoeven film from over thirty years ago: Total Recall.
In fairness, the film (we’re talking about the 1990 one starring the former governor of California not the 2012 remake) was based on a short story by Phillip K Dick. But for the purposes of this article we’ll be discussing the movie’s depiction of “Rekall,” a mysterious company portrayed in the film.

Controversy brewing?
But the site also touches on a sensitive topic in the cyber-security industry. For decades, security researchers have been secretly hacking back against malware operators.
Just like malware sometimes uses bugs in legitimate apps to infiltrate systems, security firms have also used bugs in malware code to infiltrate the attacker’s infrastructure.



The maker of a defunct cloud photo storage app that pivoted to selling facial recognition services has been ordered to delete user data and any algorithms trained on it, under the terms of an FTC settlement.
The regulator investigated complaints the Ever app — which gained earlier notoriety for using dark patterns to spam users’ contacts — had applied facial recognition to users’ photographs without properly informing them what it was doing with their selfies.
Under the proposed settlement, Ever must delete photos and videos of users who deactivated their accounts and also delete all face embeddings (i.e. data related to facial features which can be used for facial recognition purposes) that it derived from photos of users who did not give express consent to such a use.