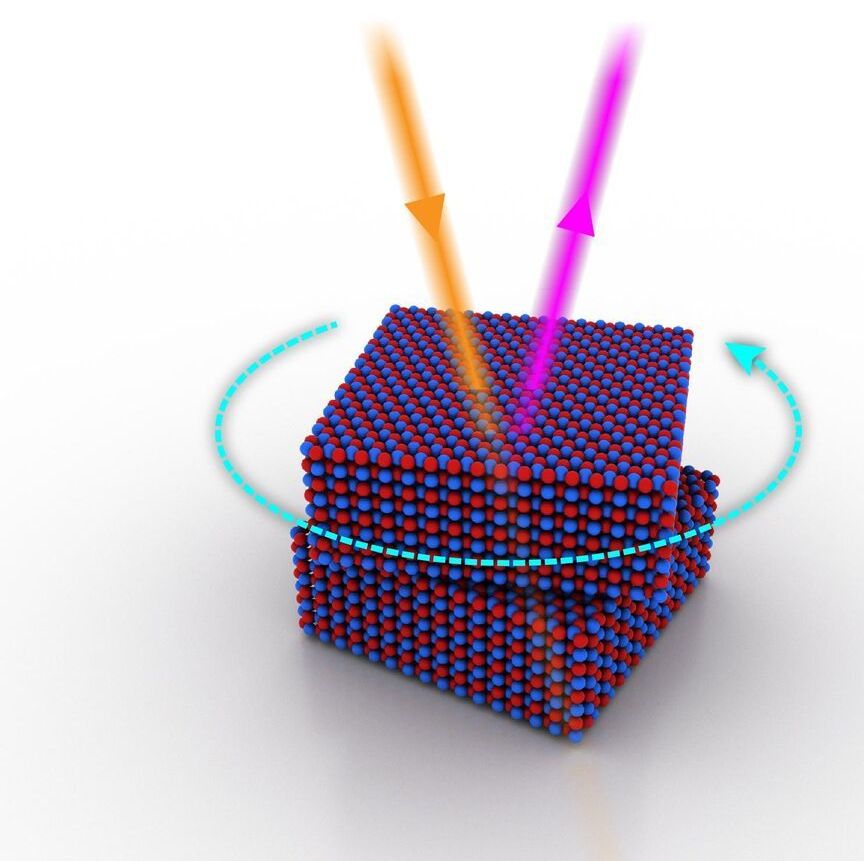
Columbia researchers engineer first technique to exploit the tunable symmetry of 2D materials for nonlinear optical applications, including laser, optical spectroscopy, imaging, and metrology systems, as well as next-generation optical quantum information processing and computing.
Nonlinear optics, a study of how light interacts with matter, is critical to many photonic applications, from the green laser pointers we’re all familiar with to intense broadband (white) light sources for quantum photonics that enable optical quantum computing, super-resolution imaging, optical sensing and ranging, and more. Through nonlinear optics, researchers are discovering new ways to use light, from getting a closer look at ultrafast processes in physics, biology, and chemistry to enhancing communication and navigation, solar energy harvesting, medical testing, and cybersecurity.
Columbia Engineering researchers report that they developed a new, efficient way to modulate and enhance an important type of nonlinear optical process: optical second harmonic generation — where two input photons are combined in the material to produce one photon with twice the energy — from hexagonal boron nitride through micromechanical rotation and multilayer stacking. The study was published online on March 32021, by Science Advances.