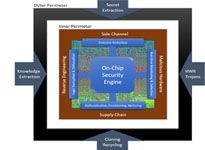
As Internet of Things (IoT) devices rapidly increase in popularity and deployment, economic attackers and nation-states alike are shifting their attention to the vulnerabilities of digital integrated circuit (IC) chips. Threats to IC chips are well known, and despite various measures designed to mitigate them, hardware developers have largely been slow to implement security solutions due to limited expertise, high cost and complexity, and lack of security-oriented design tools integrated with supporting semiconductor intellectual property (IP). Further, when unsecure circuits are used in critical systems, the lack of embedded countermeasures exposes them to exploitation. To address the growing threat this poses from an economic and national security perspective, DARPA developed the Automatic Implementation of Secure Silicon (AISS) program. AISS aims to automate the process of incorporating scalable defense mechanisms into chip designs, while allowing designers to explore chip economics versus security trade-offs based on the expected application and intent while maximizing designer productivity.
Today, DARPA is announcing the research teams selected to take on AISS’ technical challenges. Two teams of academic, commercial, and defense industry researchers and engineers will explore the development of a novel design tool and IP ecosystem – which includes tool vendors, chip developers, and IP licensors – allowing, eventually, defenses to be incorporated efficiently into chip designs. The expected AISS technologies could enable hardware developers to not only integrate the appropriate level of state-of-the-art security based on the target application, but also balance security with economic considerations like power consumption, die area, and performance.
“The ultimate goal of the AISS program is to accelerate the timeline from architecture to security-hardened RTL from one year, to one week – and to do so at a substantially reduced cost,” said the DARPA program manager leading AISS, Mr. Serge Leef.