Quantum Tech and Bank security.
BT’s research arm showcased the future of banking technology, including quantum key distribution and biometrics.


Wow — hope that folks at Apple, Samsung, Motorola, etc. see this.
In response to an incident that lacked any relation to the last fingerprint-related news, a Minnesota court ruled against a recent Fifth Amendment appeal regarding device passwords. The Minnesota Court of Appeals ruled that ordering an individual to unlock a device with a fingerprint “is no more testimonial than furnishing a blood sample, providing handwriting or voice exemplars, standing in a lineup, or wearing particular clothing.”
The case in question involved Matthew Vaughn Diamond, a man Carver County District Court found guilty in 2015 of burglary and theft, among other crimes. Other news outlets cite arrest records from far before 2015, but the records showed no relevance to the January 2017 ruling. The Carver County District Court fought Diamond over his phone’s contents—he locked the phone with a fingerprint and refused to unlock the phone for the court. He argued, initially, that forcing his fingerprint violated both his Fourth and Fifth Amendment rights. However, the Minnesota Court of Appeals heard only the Fifth Amendment appeal.
According to the Fifth Amendment, compelled self-incrimination is a violation of human rights. “The Supreme Court has held that ‘a witness may have a reasonable fear of prosecution and yet be innocent of any wrongdoing. The privilege serves to protect the innocent who otherwise might be ensnared by ambiguous circumstances’.” Additionally, the “right to remain silent” from the Miranda Rights, read to an arrestee at the time of arrest, granted a suspect the ability to refuse questions. Additionally, at the minimum, gave suspects the right to avoid answering questions legally and without fear of immediate repercussions.

Intelligence Advanced Research Projects Activity (IARPA), the intelligence community’s research arm, will soon launch two programs designed to detect fake fingerprints and develop devices to collect fingerprint data without the aid of a human operator, according to a report by GCN.
The Odin program, which is scheduled to begin with four prime developers in early March, will develop detection technologies that can spot presentation attacks on biometric devices that attempt to spoof physical biometric samples, said Chris Boehnen, senior program manager at IARPA.
Boehnen said that prosthetic fingers, fake fingerprints made with wood glue and other tactics can dupe current fingerprint sensors.

Resembling something that looks more like an Apple store than a traditional doctor’s office, Forward proposes an entirely different approach to healthcare, with unlimited access to the clinic’s medical resources through a single monthly membership fee.
Upon arriving at a Forward clinic, members sign in on an iPad and enter a custom-designed body scanner. The device immediately processes a variety of biometric data which can be accessed by members through an app on their phone.
Things get even more futuristic when you move into the clinic’s exam rooms. Faced with a giant touch screen display on the wall integrating your medical history and recent biometric data, the doctor can discuss any imminent healthcare issues while an AI system monitors the conversation and instantly displays notes and suggested treatment plans.

Has anyone besides NSA, NIST, DARPA, IARPA, etc. realize and thought about what type of cyber warfare will exist in a QC world? The skillsets alone will be so far advance than the techies that we have seen in most companies today as well as in most government agencies. Granted we’re simplifying things with the platform; however, skillsets will still need to be more advance than what we have seen with the standard techie.
Members of the cryptography community have expressed interest in the National Institute of Standards and Technology’s (NIST) recent call for an algorithm less susceptible to hacks from a computer that does not exist yet.
NIST announced a call for proposals for post-quantum cryptography standardization on Dec. 20. One or more of the proposed algorithms will ultimately replace some of NIST’s cryptographic standards that are most vulnerable to quantum computers. According to Dustin Moody, a mathematician at NIST, 40 people have joined the agency’s online cryptography forum since the call was announced two weeks ago. The forum had about 200 members before the call went out. Moody said that many people were anticipating the announcement, as cryptography enthusiasts tend to run in the same circles.
“Most people who are interested in the field already knew about it,” Moody said. “The call wasn’t a surprise.”

Federal agencies of the US government are expanding their calls for quantum computing resistant encryption methods. In effect, the National Institute of Standards (NIST) recently announced a request for public-key post-quantum algorithms. This action follows warnings from the National Security Agency (NSA) about the risks of potential quantum-based cyberattacks and the NSA’s appeal for developing post-quantum algorithms.
Also read: New Developments in Quantum Computing Impact Bitcoin
Moreover, in the near future, it might possible for anyone to manipulate the awesome power of quantum computing. The astronomical price of a quantum computer would not be a limitation because, for example, IBM is offering to the general public quantum computing via the cloud.

Whenever cybersecurity is discussed, the topic of biometric authentication rises alongside it as a better, more effective, more secure method of security. But is it? Do biometrics actually provide a safer way to complete purchase transactions online?
“Biometrics are a device-specific authentication method,” said Madeline Aufseeser, CEO of online fraud prevention company Tender Armor, of the ways biometric authentication is presently used to secure a digital purchase transaction (as opposed to logging into a bank’s web site, to view an account or transfer money). “Typically the same biometric method does not work across multiple purchasing channels today. The fingerprint used to make a purchase with a smartphone cannot necessarily be used to authenticate a phone order purchase or purchase made with a computer. When you confirm [a purchase transaction] with your fingerprint on a smartphone, all that’s saying is that’s the same fingerprint that’s allowed to use this phone, or the specific application on the phone. Because the fingerprint is only resident and stored on the phone, the phone is authenticating itself, not the cardholder conducting the transaction.”
This sounds a little odd compared to what we might have heard about the capabilities of biometrics previously, mainly because it goes against a core assumption: that a biometric identifier (like a fingerprint) goes with transactional data, from the phone or device, to the payment processor, to the merchant.

Tune in tomorrow (Thursday, Nov 10, 2016) at 4:30PM Eastern. Find out what Edward Snowden has to say on the future of the US. [Source: StartPage via Engadget]
American technology policies could change significantly under Donald Trump, and that includes its stance on privacy. How will the new leader alter government surveillance, for example? Edward Snowden might have an answer. The whistleblower and Dutch search engine StartPage are hosting a live event on November 10th at 4:30PM Eastern to address what happens to privacy in the Trump era, among other questions. Snowden speaking engagements are nothing new, but this is special — he’s more than a little familiar with government spying activities, and this is his first chance to opine on how things might be different under a new administration.
Snowden hasn’t said much of anything about the subject as of this writing. However, Trump doesn’t exactly have a stellar record on internet privacy so far. He has proposed reauthorizing the Patriot Act and the previous, less restrained NSA mass surveillance that took place while the Act was in force. He tends to “err on the side of security” over privacy, even if he’s not especially fond of it. As such, Snowden probably won’t have many kind things to say. He’s in favor of more privacy wherever possible, and that could easily put him at greater odds with the US government than he is now.
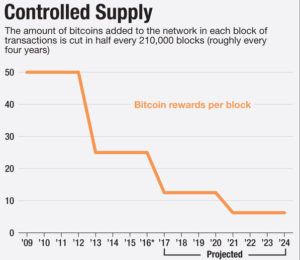
By now, most Bitcoin and Blockchain enthusiasts are aware of four looming issues that threaten the conversion of Bitcoin from an instrument of academics, criminal activity, and closed circle communities into a broader instrument that is fungible, private, stable, ubiquitous and recognized as a currency—and not just an investment unit or a transaction instrument.
These are the elephants in the room:
As an Op-Ed pundit, I value original content. But the article, below, on Bitcoin fungibility, and this one on the post-incentive era, are a well-deserved nod to inspired thinking by other writers on issues that loom over the cryptocurrency community.
This article at Coinidol comes from an unlikely source: Jacob Okonya is a graduate student in Uganda. He is highly articulate, has a keen sense of market economics and the evolution of technology adoption. He is also a quick study and a budding columnist.
What Happens When Bitcoin Mining Rewards Diminish To Zero?
Jacob addresses this last issue with clarity and focus. I urge Wild Ducks to read it. My response, below touches on both issues 3 and 4 in the impromptu list, above.
Sunset mining incentives—and also the absence of supporting fully anonymous transactions—are two serious deficiencies in Bitcoin today.
I am confident that both shortcomings will be successfully addressed and resolved.
Thoughts about Issues #3 and #4: [Disclosure] I sit on the board at CRYPSA and draft whitepapers and position statements.*
Blockchain Building: Dwindling Incentives
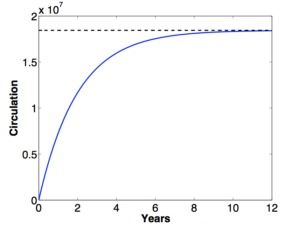 Financial incentives for miners can be replaced by non-financial awards, such as recognition, governance, gaming, stakeholder lotteries, and exchange reputation points. I am barely scratching the surface. Others will come up with more creative ideas.
Financial incentives for miners can be replaced by non-financial awards, such as recognition, governance, gaming, stakeholder lotteries, and exchange reputation points. I am barely scratching the surface. Others will come up with more creative ideas.
Last year, at the 2015 MIT Bitcoin Expo, Keynote speaker Andreas Antonopoulos expressed confidence that Bitcoin will survive the sunset of miner incentives. He proposed some novel methods of ongoing validation incentives—most notably, a game theory replacement. Of course, another possibility is the use of very small transaction fees to continue financial incentives.
Personally, I doubt that direct financial incentives—in the form of microcash payments— will be needed. Ultimately, I envision an ecosystem in which everyone who uses Bitcoin to buy, sell, gift, trade, or invest will avoid fees while creating fluidity—by sharing the CPU burden. All users will validate at least one Blockchain transaction for every 5 transactions of their own.
Today, that burden is complex by design, because it reflects increasing competition to find a diminishing cache of unmined coins. But without that competition, the CPU overhead will be trivial. In fact, it seems likely that a validation mechanism could be built into every personal wallet and every mobile device app. The potential for massive crowd-sourced scrutiny has the added benefit of making the blockchain more robust: Trusted, speedy, and resistant to attack.
Transaction Privacy & Anonymity
Bitcoin’s lack of rock-solid, forensic-thwarting anonymity is a weak point that must ultimately be addressed. It’s not about helping criminals, it’s about liberty and freedoms. Detectives & forensic labs have classic methods of pursuing criminals. It is not our job to offer interlopers an identity, serial number and traceable event for every transaction.
Anonymity can come in one of three ways. Method #3 is least desirable:
 and earnest but misguided attempts to create a registry of ‘tainted’ coins.
and earnest but misguided attempts to create a registry of ‘tainted’ coins.That’s my opinion on the sunset of mining incentives and on transaction anonymity.
—What’s yours?
* Philip Raymond is co-chair of the Cryptocurrency Standards
Association. He was host and MC for the Bitcoin Event in New York.
I was pointed to this article by Jon Matonis, Founding Director, Bitcoin Foundation. I was sufficiently moved to highlight it here at Lifeboat Foundation, where I am a contributing writer.
On Fungibility, Bitcoin, Monero and ZCash … [backup]
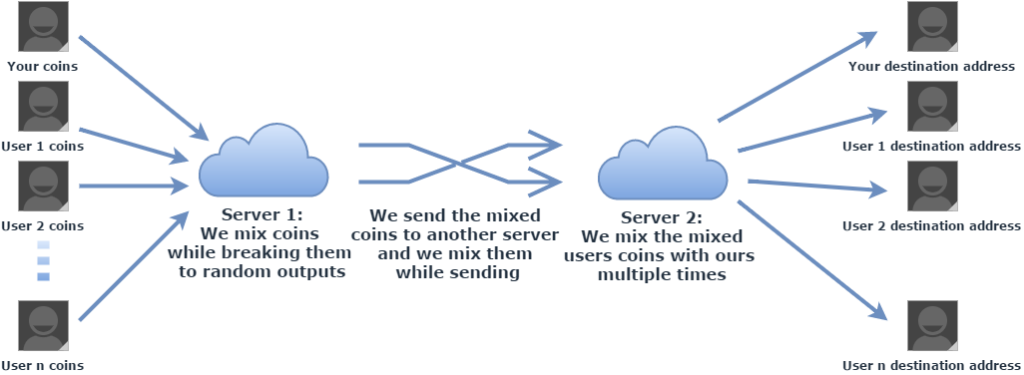
This is among the best general introductions I have come across on traceability and the false illusion of privacy. The explanation of coin mixing provides and excellent, quick & brief overview.
Regarding transaction privacy, a few alt-coins provide enhanced immunity or deniability from forensic analysis. But if your bet is on Bitcoin (as it must be), the future is headed toward super-mixing and wallet trading by desgin and by default. Just as the big email providers haved added secure transit,
Bitcoin will eventually be fully randomized and anonymized per trade and even when assets are idle. It’s not about criminals; it’s about protecting business, government and individuals. It’s about liberty and our freedoms. [Continue below image]
The next section of the article explains the danger of losing fungibility due to transaction tracing and blacklisting. I can see only ONE case for this, and it requires a consensus and a hard fork (preferably a consensus of ALL stakeholders and not just miners). For example, when a great number of Etherium was stolen during the DAO meltdown.
My partner, Manny Perez, and I take opposing views of blacklisting coins based on their ‘tainted’ history (according to “The Man”, of course!). I believe that blacklists must ultimately be rendered moot by ubiquitous mixing, random transaction-circuit delays,  and multiple-transaction ‘washing’ (intentionally invoking a term that legislators and forensic investigators hate)—Manny feels that there should be a “Law and Order” list of tainted coins. Last year, our Pro-&-Con views were published side-by-side in this whitepaper.
and multiple-transaction ‘washing’ (intentionally invoking a term that legislators and forensic investigators hate)—Manny feels that there should be a “Law and Order” list of tainted coins. Last year, our Pro-&-Con views were published side-by-side in this whitepaper.
Finally, for Dogbert’s take on fungible, click here. I bought the domain fungible.net many years ago, and I still haven’t figured out what to do with it. Hence this Dilbert cartoon. smile
____________
Philip Raymond is co-chair of The Cryptocurrency Standards Association.
He also presents on privacy, anonymity, blind signaling & antiforensics.