We know what you’re thinking: “What if America loses the race for 5G!?”
And also: “What is 5G?”
Full episode: https://on.cc.com/30Cc9Q6

We know what you’re thinking: “What if America loses the race for 5G!?”
And also: “What is 5G?”
Full episode: https://on.cc.com/30Cc9Q6

A group of security researchers has found that some cameras are vulnerable to ransomware attacks via Wi-Fi or hijacked computers (using the USB connection) that can render a camera and its photos entirely usage until a sum of money is paid to the hackers.
Check Point Software Technologies has shown (as seen in the video above) that Canon DSLRs (it’s not clear if other cameras are also affected) are susceptible to ransomware attacks, an increasingly common exploitation in which a hacker disables a device until the owner pays a ransom to regain control. As more and more electronics gain internet connectivity, these attacks are becoming more common, particularly since manufacturers typically don’t put the same sort of effort into fortifying the network security of small electronics as they do into computers. Canon released a statement in which they offered some barebones tips to avoid being susceptible to these attacks and noted that there have been no known instances of such an attack occurring. They did not indicate whether they plan to fix the vulnerabilities through firmware updates, so it probably doesn’t hurt to be a bit more careful to protect your photos.

Iron Ox has just opened its first fully automated farm in San Carlos, California. The company claims that their hydroponic system can produce 30 times the yield per acre of land comparing to traditional farms, while using 90% less water.
► Subscribe for more tech & culture videos: http://on.mash.to/subscribe ◄
MORE FROM MASHABLE
• Video — https://youtu.be/6ElleCub6uM
• Video — https://youtu.be/jAu1ZsTCA64
• Video — https://youtu.be/W8T6fYt9-tA
Best of playlist: https://on.mash.to/BestOf
MASHABLE ACROSS THE WEB
Mashable.com: http://on.mash.to/1hCcRpl
Facebook: http://on.mash.to/2lyOwmZ
Twitter: http://on.mash.to/1Udp1kz
Instagram: http://on.mash.to/1U6D40z
Mashable is for superfans. We’re not for the casually curious. Obsess with us.

Two trends that are dominating the technology industry are the Internet of Things (IoT) and Artificial Intelligence (AI). But for industrial automation, these two technologies are much more than the buzzwords or trending topics. The convergence of AI and IoT will redefine the future of industrial automation. It is set to lead the Industry 4.0 revolution.
IoT and AI are two independent technologies that have a significant impact on multiple industry verticals. While IoT is the digital nervous system, AI becomes the brain that makes decisions which control the overall system. The lethal combination of AI and IoT brings us AIoT — Artificial Intelligence of Things — that delivers intelligent and connected systems that are capable of self-correcting and self-healing themselves.
To appreciate the promise of AIoT, we need to look at the evolution of connected systems.

Tech billionaire Peter Thiel painted a gloomy picture of artificial intelligence in his NYT’s op-ed on Thursday, detailing the technology’s real value and purpose as primarily a military one.
“The first users of the machine learning tools being created today will be generals,” Thiel declared in his 1,200-word piece. “A.I. is a military technology.”
Thiel’s portrayal is a far cry from the optimistic view that many in Silicon Valley have embraced. Artificial intelligence has promised to give us the next, best Netflix recommendations, let us search the internet using our voices, and do away with humans behind the wheel. It’s also expected to have a huge impact in medicine and agriculture. But instead, Thiel says that AI’s real home is on the battlefield — whether that be in the physical or cyber worlds.

China has declared its ambition to dominate the technology sector from 5G and artificial intelligence to robotics and quantum computing. Joining the infrastructure firms on this year’s list are technology firms such as Alibaba, http://JD.com/, Tencent, Xiaomi, and BOE. Huawei was not included as it is a private entity.
China’s ambition to dominate the technology sector from 5G and artificial intelligence to robotics and quantum computing is bearing fruit.

In 1948, physicist Leonard Eisenbud proposed a particular way of transmitting the waves to overcome this. But not until now have researchers made it happen.
By Michael Slezak.
It’s a call with no response. A new way of creating waves – whether of light, radio or sound – that don’t echo promises to improve everything from your Wi-Fi signal to medical imaging to shining lasers through space.
As a wave travels – think of light shining through water, for example – it can become scattered. This is a problem in telecommunications: if you send digital signals down a very long optical fibre, the pulses can get stretched out, and 1s can start to blend into 0s.

Warnings about connected vehicle vulnerabilities have been a steady drumbeat for years. Now a consumer-advocacy group is putting it in starker terms, suggesting a mass cyberattack against such vehicles could lead to Sept. 11-level casualties.
California-based Consumer Watchdog has issued a 49-page report that paints the dire picture and urges automakers to install 50-cent “kill switches” to allow vehicles to be disconnected from the Internet. The report highlights numerous widely reported instances of remote vehicle hacking, such as a 2015 demonstration involving a Jeep Cherokee left crawling along a St. Louis-area freeway.
“Millions of cars on the internet running the same software means a single exploit can affect millions of vehicles simultaneously. A hacker with only modest resources could launch a massive attack against our automotive infrastructure, potentially causing thousands of fatalities and disrupting our most critical form of transportation,” the group warns.

In the premiere of the HBO/BBC miniseries Years and Years, two parents are worried. Their teenage daughter Bethany has been hiding behind a 3D animated emoji mask and has scheduled a talk with them. Trying to figure out what they’re up against, they sneak a peek at her internet searches. When they discover that she’s been searching for information about being trans, they’re relieved; they can handle a transgender child.
Except when it comes time for their talk, Bethany tells her parents she’s transhuman and that she wants to “live forever as information.” The show represents transhumanist technology and aspirations, many of which revolve around upgrading and digitizing the human body, as a movement that will bring positive, negative, and downright confusing implications, ultimately changing the human race. The real question is what exactly that means. Humans opened the Pandora’s box of merging technology and biology a long time ago, and we’re now speeding head-on into the consequences, despite not knowing what humanity will become.
Bethany’s “coming out” scene hinges on the fact that the changes she desires are far more dangerous—and, for her parents, far more difficult to stomach—than gender reassignment. Bethany’s excitement at escaping the mortal coil brims with typical teenage naïveté: “Transhumans are not male or female, but better,” she tells her parents. For Bethany, that means no longer being human. “I will be data!” she enthuses.
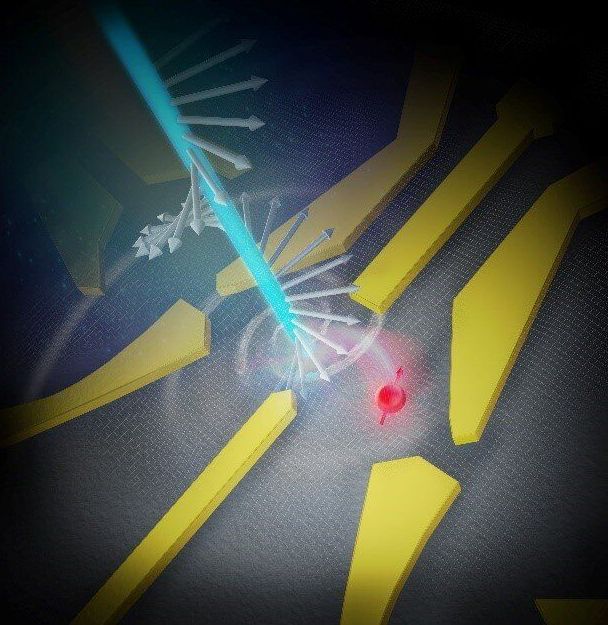
A research team lead by Osaka University demonstrated how information encoded in the circular polarization of a laser beam can be translated into the spin state of an electron in a quantum dot, each being a quantum bit and a quantum computer candidate. The achievement represents a major step towards a “quantum internet,” in which future computers can rapidly and securely send and receive quantum information.
Quantum computers have the potential to vastly outperform current systems because they work in a fundamentally different way. Instead of processing discrete ones and zeros, quantum information, whether stored in electron spins or transmitted by laser photons, can be in a superposition of multiple states simultaneously. Moreover, the states of two or more objects can become entangled, so that the status of one cannot be completely described without this other. Handling entangled states allow quantum computers to evaluate many possibilities simultaneously, as well as transmit information from place to place immune from eavesdropping.
However, these entangled states can be very fragile, lasting only microseconds before losing coherence. To realize the goal of a quantum internet, over which coherent light signals can relay quantum information, these signals must be able to interact with electron spins inside distant computers.