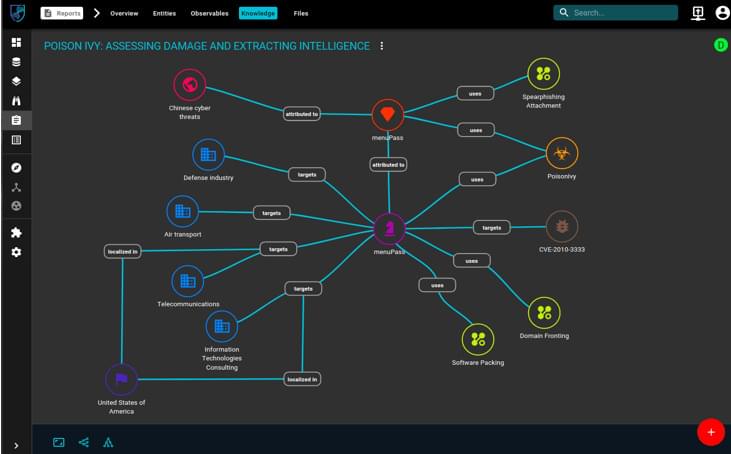
OpenCTI-An Open Source Cyber Threat Intelligence Platform. OpenCTI allowing organizations to manage their Cybe Threat Intelligence observables.
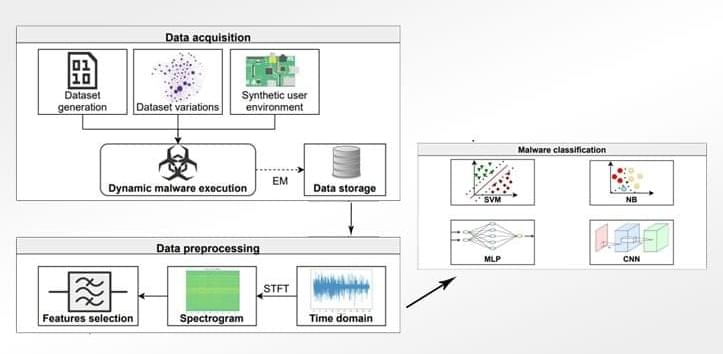
OpenCTI is an open source platform allowing organizations to manage their cyber threat intelligence knowledge and observables. It has been created in order to structure, store, organize and visualize technical and non-technical information about cyber threats.
The structuralist of the data is performed using a knowledge schema based on the STIX2 standards. It has been designed as a modern web application including a GraphQL API and an UX oriented frontend. Also, OpenCTI can be integrated with other resources and applications such as MISP, TheHive, MITRE ATTACK, etc.
The goal is to create a comprehensive software allowing users to capitalize technical (such as TTPs and observables) and non-technical information (such as suggested attribution, victimlogy etc.) while linking each piece of information to its primary source (a report, a MISP event, etc.), with features such as links between each information, first and last seen dates, levels of confidence etc.