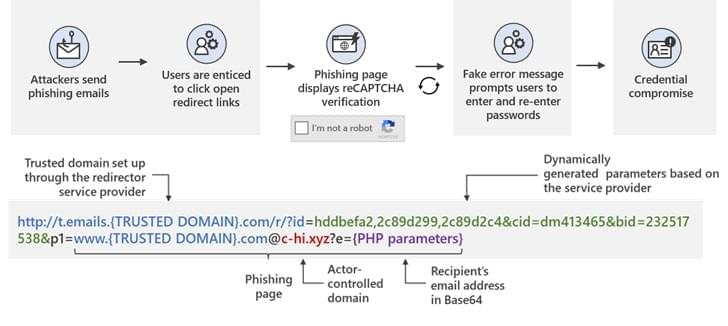
Microsoft is warning of a widespread credential phishing campaign that leverages open redirector links.


A blockchain-based initiative from the United States Air Force will employ Constellation’s Hypergraph Network to provide data security with the Department of Defense’s commercial partners.
In a Thursday announcement, Constellation said it had been working with Kinnami Software Corporation to develop an end-to-end data security solution using blockchain encryption and distributed data management for the United States Transportation Command, Air Mobility Command’s 618th Air Operations Center, and a Civil Reserve Air Fleet partner. According to the platform, its goal is to securely exchange data with commercial partners on missions involving the operations of aircraft and ships under contract to the Department of Defense, or DoD.
The United States Transportation Command, or USTRANSCOM, allows authorities — including those in the 618th — to coordinate missions using available resources from both the military and private sector. Constellation Network’s solution may have the potential to improve the existing cybersecurity and general effectiveness.


A dangerous vulnerability in Realtek chipsets used in hundreds of thousands of smart devices from at least 65 vendors is currently under attack from a notorious DDoS botnet gang.
The attacks started last week, according to a report from IoT security firm SAM, and began just three days after fellow security firm IoT Inspector published details about the vulnerability on its blog.
Tracked as CVE-2021–35395, the vulnerability is part of four issues IoT Inspector researchers found in the software development kit (SDK) that ships with multiple Realtek chipsets (SoCs).

The ‘Joker’ virus hides in several apps on the Google Play Store and the user does not realize it until their bank accounts are emptied. See how this malware operates and what are the dangerous applications.
In September 2,020 the ’Joker’ virus was found in 24 Android applications that registered more than 500 thousand downloads before being removed. It is estimated that that time it affected more than 30 countries including the United States, Brazil and Spain. Through unauthorized subscriptions, hackers could steal up to $7 (about 140 Mexican pesos) per subscription weekly, a figure that has most likely increased in recent months.
How does the Joker virus work in Android apps?
The ’Joker’ Trojan virus belongs to a family of malware known as Bread 0 whose objective is to hack cell phone bills and authorize operations without the user’s consent.

THE personal records of 38million people were accidentally leaked on the open internet due to a flaw in more than a thousand Microsoft web apps, according to reports.
American Airlines, Ford, J.B. Hunt, the Maryland Department of Health, the New York City Municipal Transportation Authority, and New York City public schools were among the companies and organizations affected by the mistake.
The data mistakenly shared online included information from a number of Covid-19 contact tracing platforms, vaccination sign-ups, job application portals, and employee databases, according to Wired.

A Razer Synapse zero-day vulnerability has been disclosed on Twitter, allowing you to gain Windows admin privileges simply by plugging in a Razer mouse or keyboard.
Razer is a very popular computer peripherals manufacturer known for its gaming mouses and keyboards.
When plugging in a Razer device into Windows 10 or Windows 11 the operating system will automatically download and begin installing the Razer Synapse software on the computer. Razer Synapse is software that allows users to configure their hardware devices, set up macros, or map buttons.

A new ransomware gang known as LockFile encrypts Windows domains after hacking into Microsoft Exchange servers using the recently disclosed ProxyShell vulnerabilities.
ProxyShell is the name of an attack consisting of three chained Microsoft Exchange vulnerabilities that result in unauthenticated, remote code execution.
The three vulnerabilities were discovered by Devcore Principal Security Researcher Orange Tsai, who chained them together to take over a Microsoft Exchange server in April’s Pwn2Own2021hacking contest.
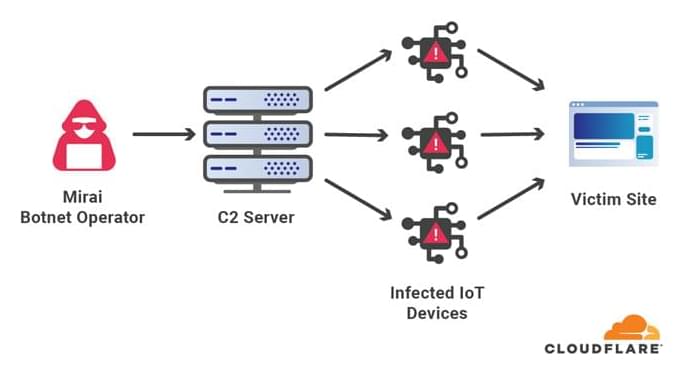
Web infrastructure and website security company Cloudflare on Thursday disclosed that it mitigated the largest ever volumetric distributed denial of service (DDoS) attack recorded to date.
The attack, launched via a Mirai botnet, is said to have targeted an unnamed customer in the financial industry last month. “Within seconds, the botnet bombarded the Cloudflare edge with over 330 million attack requests,” the company noted, at one point reaching a record high of 17.2 million requests-per-second (rps), making it three times bigger than previously reported HTTP DDoS attacks.

Uptycs Threat Research Team has discovered malware that not only hijacks vulnerable *nix-based servers and uses them to mine cryptocurrency but actually modifies their CPU configurations in a bid to increase mining performance at the cost of performance in other applications.
Perpetrators use a Golang-based worm to exploit known vulnerabilities like CVE-2020–14882 (Oracle WebLogic) and CVE-2017–11610 (Supervisord) to gain access to Linux systems, reports The Record. Once they hijack a machine, they use model-specific registers (MSR) to disable the hardware prefetcher, a unit that fetches data and instructions from the memory into the L2 cache before they are needed.