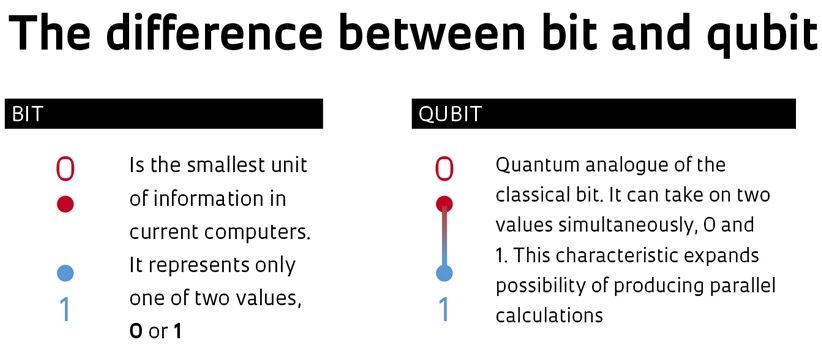
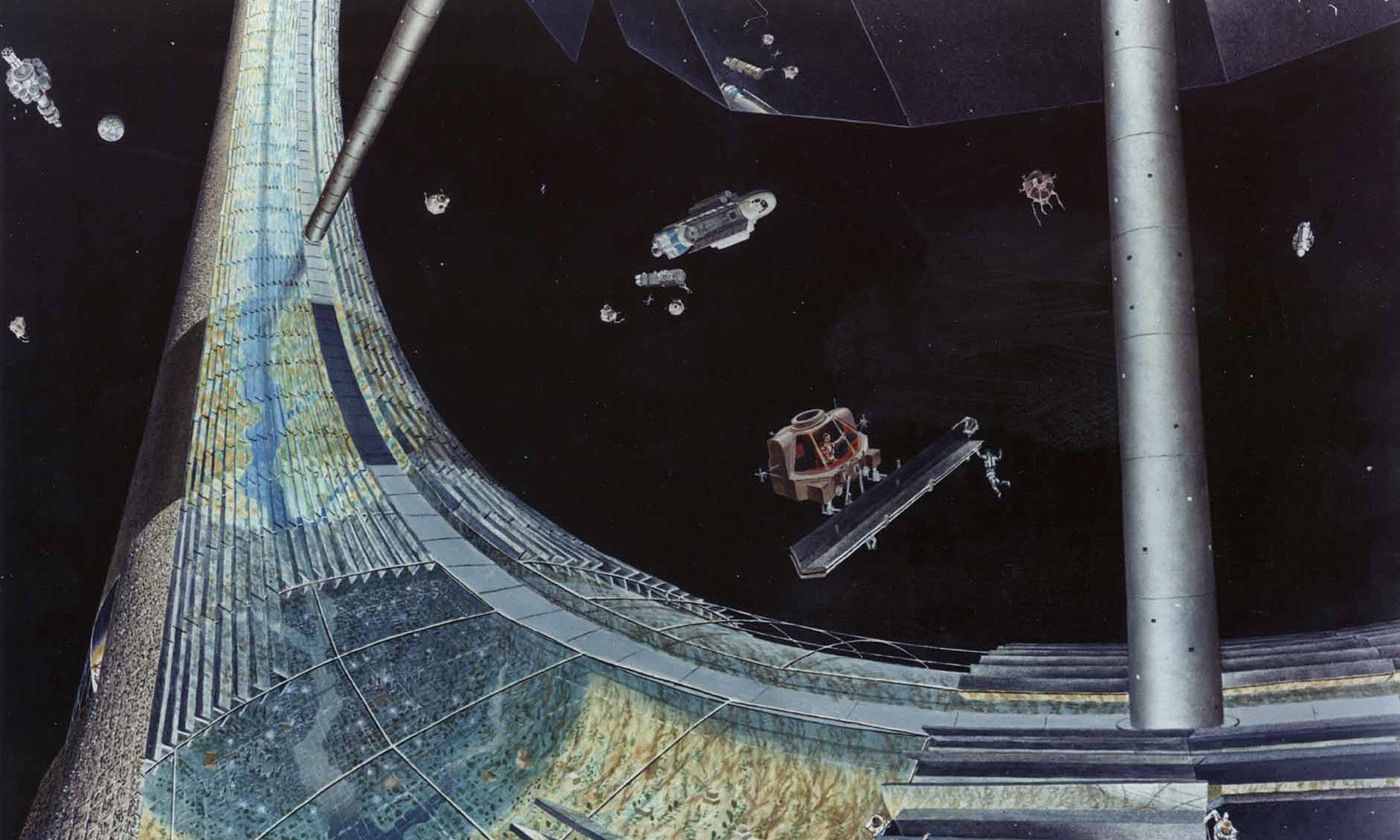
If human beings are ever to colonise other planets – which might become necessary for the survival of the species, given how far we have degraded this one – they will almost certainly have to use generation ships: spaceships that will support not just those who set out on them, but also their descendants. The vast distances between Earth and the nearest habitable planets, combined with the fact that we are unlikely ever to invent a way of travelling that exceeds the speed of light, ensures that many generations will be born, raised and die on board such a ship before it arrives at its destination.
A generation ship would have to be a whole society in microcosm, with hospitals and schools, living quarters and perhaps entertainment districts, a security force, maybe even a judiciary. It would need to be able to provide food for its crew, and that might require agriculture or aquaculture, perhaps even domestic animals (which might also be needed for the colonisation effort). Its design therefore presents a major challenge: not just to engineers but also to social scientists. How should the crew be selected and the environment structured to minimise interpersonal conflict? What size of population is optimal for it to remain committed to the single overarching project of colonising a new planet without too much of a risk of self-destructive boredom or excessive narrowing of the gene pool? Does mental health require that a quasi-natural environment be recreated within the ship (with trees, grass and perhaps undomesticated birds and small animals)?
As well as the technological and social challenges confronting the designers of such ships, there are fascinating philosophical and ethical issues that arise. The issue I want to focus on concerns the ethics of a project that locks the next generation into a form of living, the inauguration of which they had no say over, and that ensures their options are extremely limited.
Read more