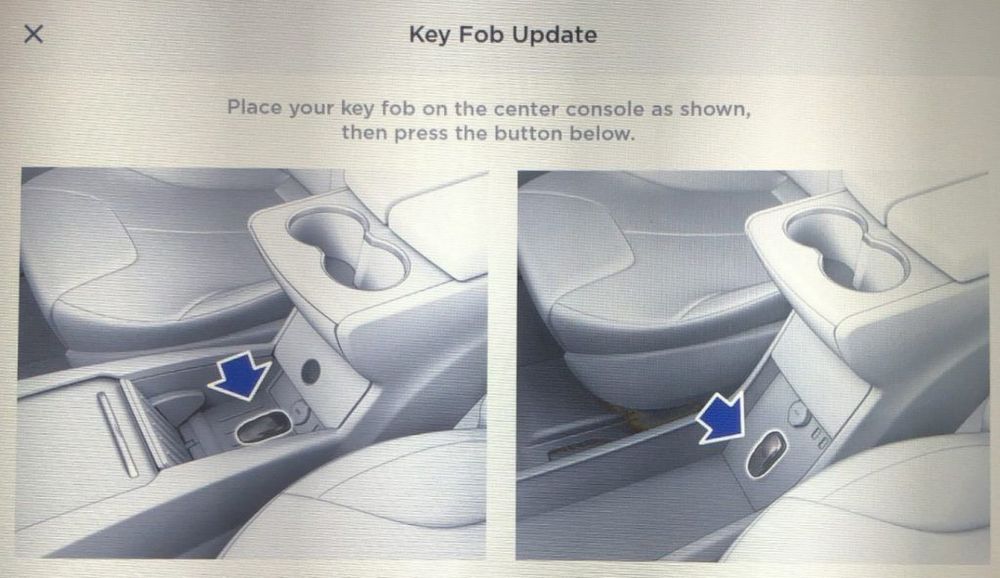
As part of continuing efforts to ensure their vehicles are the safest cars on the road, Tesla’s “Bug Bounty” program gives awards to security researchers that uncover vulnerabilities in the company’s various product systems. Perhaps one of the most impressive parts of that program, however, is Tesla’s ability to remedy the flaws quickly. In the most recent example of their dedication to security, a Bug Bounty find from April this year is now being patched via an over-the-air (OTA) update in 2019.32.
Last year, a Tesla Model S key fob was hacked by a team led by Lennert Wouters of Katholieke Universiteit Leuven in Belgium (KU Leuven). The security flaw enabled would-be car thieves to clone a fob in less than two seconds, after which the vehicle could be driven off. Tesla subsequently offered a multi-part fix: PIN to Drive, a software update, and a new fob. Wouters again found a very similar flaw in the new fob, but this time the fix only required an OTA update which patched both the vehicle software and the fob’s configuration via radio waves.