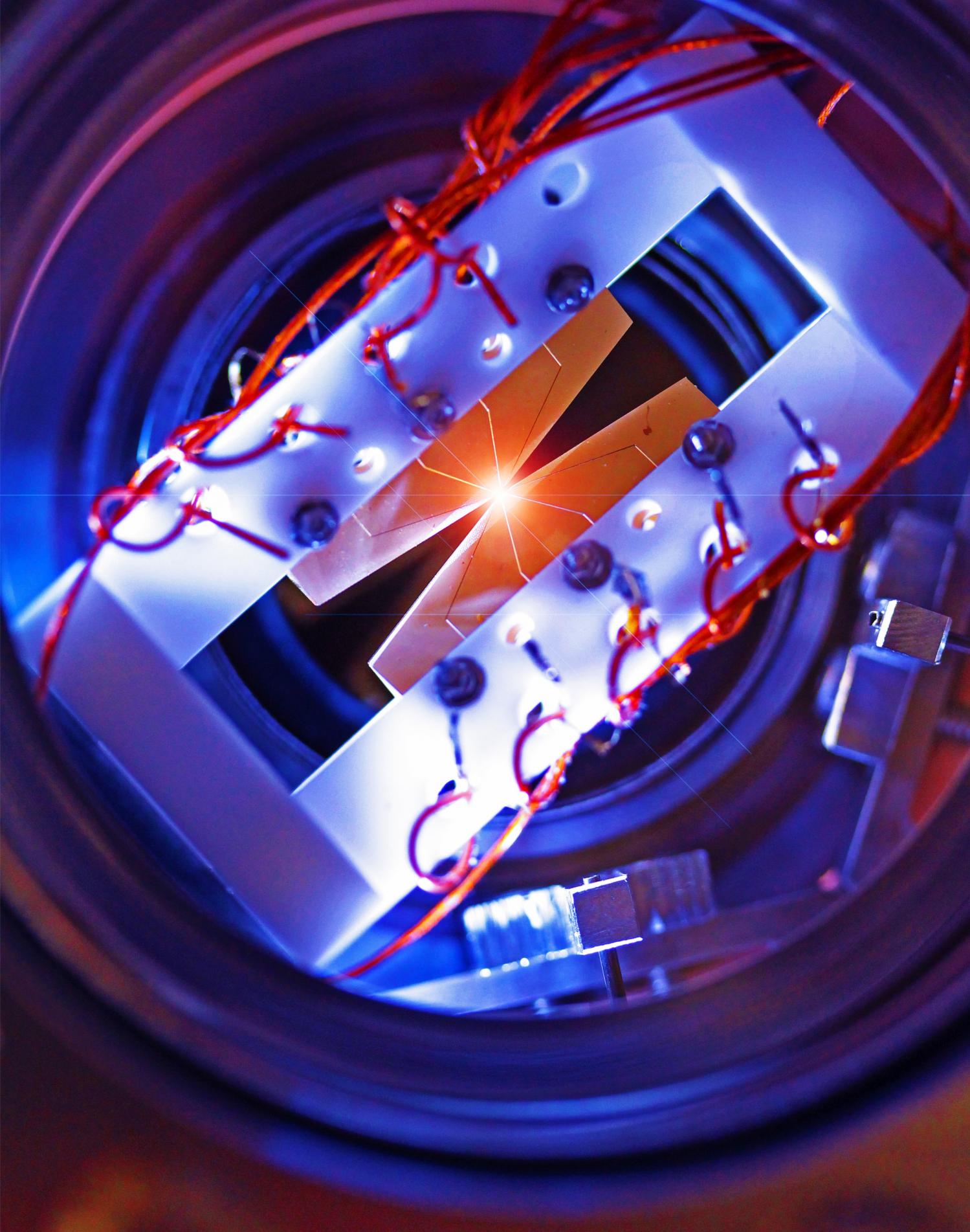
Quantum computing remains mysterious and elusive to many, but USC Viterbi School of Engineering researchers might have taken us one step closer to bring such super-powered devices to practical reality. The USC Viterbi School of Engineering and Information Sciences Institute is home to the USC-Lockheed Martin Quantum Computing Center (QCC), a super-cooled, magnetically shielded facility specially built to house the first commercially available quantum optimization processors — devices so advanced that there are currently only two in use outside the Canadian company D-Wave Systems Inc., where they were built: The first one went to USC and Lockheed Martin, and the second to NASA and Google.
Quantum computers encode data in quantum bits, or “qubits,” which have the capability of representing the two digits of one and zero at the same time — as opposed to traditional bits, which can encode distinctly either a one or a zero. This property, called superposition, along with the ability of quantum states to “interfere” (cancel or reinforce each other like waves in a pond) and “tunnel” through energy barriers, is what may one day allow quantum processors to ultimately perform optimization calculations much faster than is possible using traditional processors. Optimization problems can take many forms, and quantum processors have been theorized to be useful for a variety of machine learning and big data problems like stock portfolio optimization, image recognition and classification, and detecting anomalies. Yet, exactly because of the exotic way in which quantum computers process information, they are highly sensitive to errors of different kinds.
Read more