For Sale: A Scylex malware Kit please contact your nearest Dark Web for details.
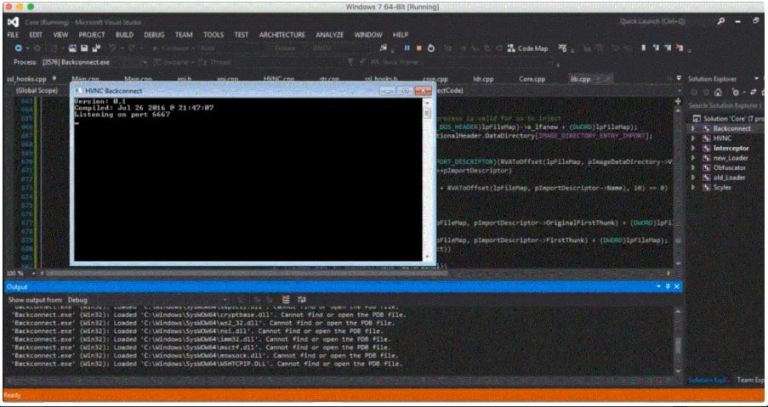
Experts from Heimdal security firm discovered a new crimeware kit, the Scylex malware kit, that aims to provide Zeus-grade Capabilities.
Security experts from the Heimdal security firm have discovered a new DIY financial crime kit offered for sale on a notorious malicious hacker forum on the dark web called Lampeduza.
The new crime kit, dubbed Scylex malware kit, allows cyber criminals to roll their own ZeuS-like malware. The malware implements the features of common banking trojan, such as stealing online banking passwords, intercept web traffic and of course establish a backdoor on the infected Windows-based machine.