Government news resource covering technology, performance, employment, telework, cybersecurity, and more for federal employees.



The attack on Rockport is one example in a rising tide of similar invasions of municipal systems across the U.S.—from major cities like Atlanta, which got hit in March, to counties, tiny towns and even a library system in St. Louis. Local governments are forced to spend money on frantic efforts to recover data, system upgrades, cybersecurity insurance and, in some cases, to pay their online extortionists if they can’t restore files some other way.
Hackers are targeting small towns’ computer systems, with public-sector attacks appearing to be rising faster than those in the private sector. Online extortionists demand bitcoin ransom in return for decryption keys.

As the Equifax hack last year showed, there’s a lack of legislation governing what happens to data from a breach. And ultimately, a breach of genetic data is much more serious than most credit breaches. Genetic information is immutable: Vigna points out that it’s possible to change credit card numbers or even addresses, but genetic information cannot be changed. And genetic information is often shared involuntarily. “Even if I don’t use 23andMe, I have cousins who did, so effectively I may be genetically searchable,” says Ram. In one case, an identical twin having her genetic data sequenced created a tricky situation for her sister.
This week, DNA testing service MyHeritage revealed that hackers had breached 92 million of its accounts. Though the hackers only accessed encrypted emails and passwords — so they never reached the actual genetic data — there’s no question that this type of hack will happen more frequently as consumer genetic testing becomes more and more popular. So why would hackers want DNA information specifically? And what are the implications of a big DNA breach?
One simple reason is that hackers might want to sell DNA data back for ransom, says Giovanni Vigna, a professor of computer science at UC Santa Barbara and co-founder of cybersecurity company Lastline. Hackers could threaten to revoke access or post the sensitive information online if not given money; one Indiana hospital paid $55,000 to hackers for this very reason. But there are reasons genetic data specifically could be lucrative. “This data could be sold on the down-low or monetized to insurance companies,” Vigna adds. “You can imagine the consequences: One day, I might apply for a long-term loan and get rejected because deep in the corporate system, there is data that I am very likely to get Alzheimer’s and die before I would repay the loan.”
MyHeritage doesn’t offer health or medical tests, but many companies, like 23andMe and Helix, do. And there are plenty of players interested in DNA: researchers want genetic data for scientific studies, insurance companies want genetic data to help them calculate the cost of health and life insurance, and police want genetic data to help them track down criminals, like in the recent Golden State Killer case. Already, we lack robust protections when it comes to genetic privacy, and so a genetic data breach could be a nightmare. “If there is data that exists, there is a way for it to be exploited,” says Natalie Ram, a professor of law focusing on bioethics issues at the University of Baltimore.
S cientists have created the UK’s first ever “unhackable” fibre network in anticipation of the dawn of quantum computers, a technology that could render current security systems completely useless and leave critical infrastructure, banking and healthcare networks open to hackers.
The network, constructed by researchers from BT, the University of York and the University of Cambridge over the past two years, is secured by the laws of quantum physics which dictate how light and matter behave at a fundamental level. Using this, it is able to block anyone attempting to crack into the fibre link.
This could be a game changer for the healthcare and financial sector, when it is feared existing encryption…

In a profound talk about technology and power, author and historian Yuval Noah Harari explains the important difference between fascism and nationalism — and what the consolidation of our data means for the future of democracy. Appearing as a hologram live from Tel Aviv, Harari warns that the greatest danger that now faces liberal democracy is that the revolution in information technology will make dictatorships more efficient and capable of control. “The enemies of liberal democracy hack our feelings of fear and hate and vanity, and then use these feelings to polarize and destroy,” Harari says. “It is the responsibility of all of us to get to know our weaknesses and make sure they don’t become weapons.” (Followed by a brief conversation with TED curator Chris Anderson)
Check out more TED Talks: http://www.ted.com
The TED Talks channel features the best talks and performances from the TED Conference, where the world’s leading thinkers and doers give the talk of their lives in 18 minutes (or less). Look for talks on Technology, Entertainment and Design — plus science, business, global issues, the arts and more.
Follow TED on Twitter: http://www.twitter.com/TEDTalks
Like TED on Facebook: https://www.facebook.com/TED
E xperts are suggesting quantum computing may render blockchain obsolete. As the tech giants such as Google and IBM are showing interest in Quantum computing the danger is evident. According to MIT Technology Review, this type of computing can hack the cryptography hash that universally secures the blockchain and in general the internet. This would suggest quantum computers may complete fraudulent transactions and steal coins. With its exponential power, quantum computers threaten blockchain’s future security.
Blockchain consists of encrypted nodes connected on a chain, which currently makes it almost impossible to hack. The order of entries adheres to the blockchain protocol, which makes it counterfeit-resistant.
To successfully hack a blockchain, you would need to alter both the targeted block and all of the blocks connected. Blockchains are synced throughout a peer-to-peer network. In this type of system, there is no central point of failure for hackers to penetrate. For a hacker to have a chance of penetrating the network, they would need to simultaneously alter at least 51% of the blockchain.

Pichai’s challenge is to find a way of reconciling Google’s dovish roots with its future. Having spent more than a decade developing the industry’s most formidable arsenal of AI research and abilities, Google is keen to wed those advances to its fast-growing cloud-computing business. Rivals are rushing to cut deals with the government, which spends billions of dollars a year on all things cloud. No government entity spends more on such technology than the military. Medin and Alphabet director Schmidt, who both sit on the Pentagon’s Defense Innovation Board, have pushed Google to work with the government on counter-terrorism, cybersecurity, telecommunications and more.
To win in the business of cloud computing, the company tiptoes into the business of war. Some staff fear it’s a first step toward autonomous killing machines.

Critical infrastructure, entertainment, finance, healthcare, telecoms, among recent targets of the Lazarus Group, aka Hidden Cobra.
On the eve of a historic summit with its rival neighbor South Korea and possible subsequent talks with the US President Donald Trump in the coming weeks, North Korea continues full-steam ahead in its mission to gather intelligence and generate income for the regime via its notorious nation-state hacking machine.
North Korea’s pervasive Lazarus Group, aka Hidden Cobra, was recently discovered ramping up a global cyber espionage campaign dubbed Operation GhostSecret, stealing information from organizations in the critical infrastructure, entertainment, finance, healthcare, and telecommunications sectors. Researchers from McAfee unearthed the wave of attacks, which they say first started with targeted hacks of banks in Turkey last month.
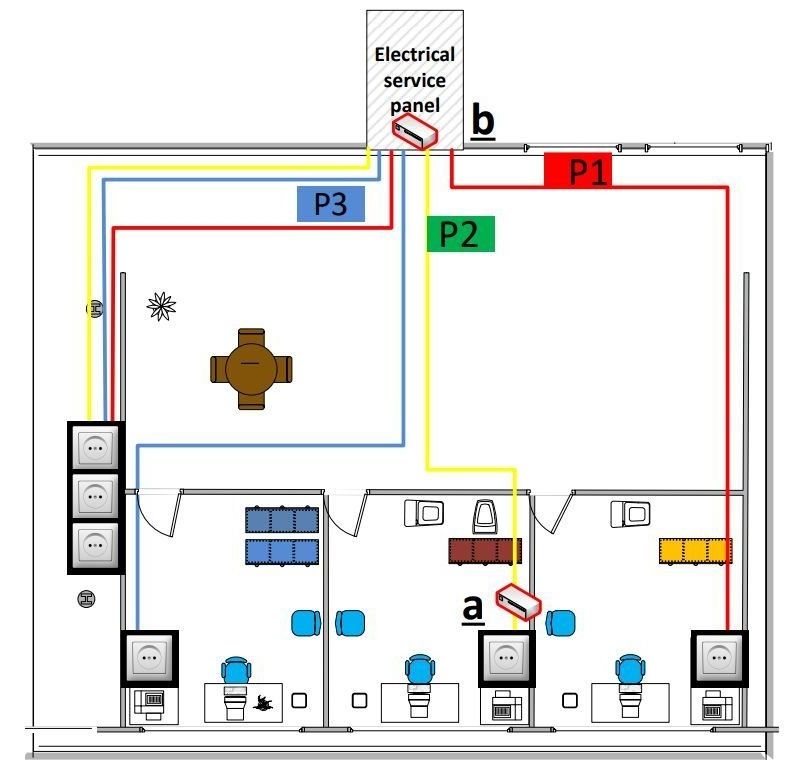
I remember this was like the plot to the Al Pacino CIA movie from the ‘90’s. Guess they actually figured out how to dial in on power lines.
Can security sleuths ever complain there’s nothing left to do? The answer is obvious, and one more path to mischief has been recognized in the form of power supplies serving as a data exfiltration tool. It appears that malware using power lines could exfiltrate data from air-gapped computers.
Researchers from the Ben-Gurion University of the Negev discovered malware that nabs data through power lines.
“PowerHammer works by infecting an air-gapped computer with malware that intentionally alters CPU utilization levels to make the victim’s computer consume more or less electrical power,” said Catalin Cimpanu, BleepingComputer. Wait, air-gapped computers?