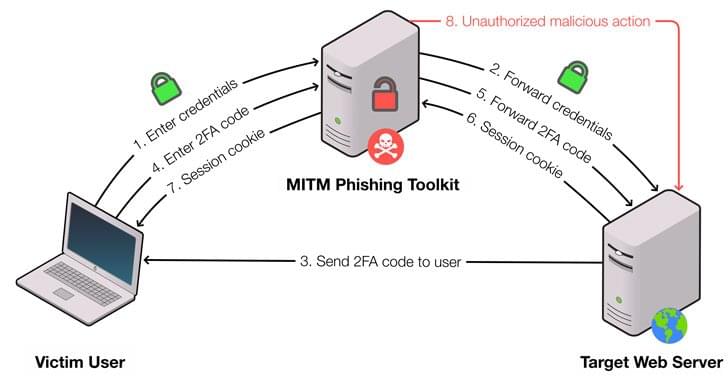
Apple has filed a federal lawsuit against Israeli spyware firm NSO Group for illegally targeting users with the Pegasus malware.



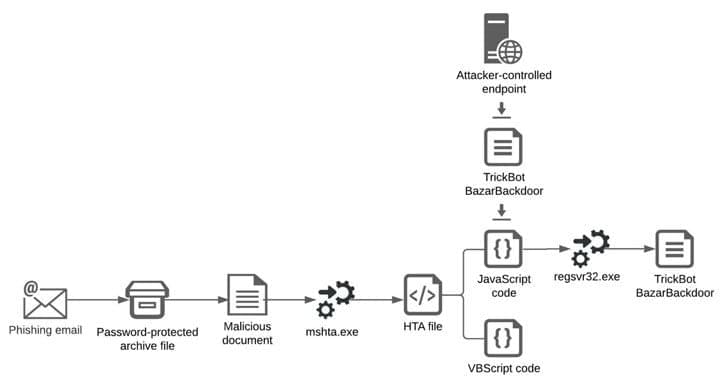
Threat actors are hacking Microsoft Exchange servers using ProxyShell and ProxyLogon exploits to distribute malware and bypass detection using stolen internal reply-chain emails.
When threat actors conduct malicious email campaigns, the hardest part is to trick users into trusting the sender enough so that they open up linked to or included malware-distributing attachments.
TrendMicro researchers have discovered an interesting tactic used of distributing malicious email to a company’s internal users using the victim’s compromised Microsoft exchange servers.

Cher sang about manipulating it while Doctor Who dramatized it. This hacker went one better and did it. Here’s how time got hacked.
During a 1961 address to the National Association of Manufacturers in New York City, John F. Kennedy said that “we must use time as a tool, not as a couch.” Fast forward fifty years, and one hacker has demonstrated exactly how to do that: by hacking time.
What is time anyway? What is time? That’s not an easy question to answer definitively.
Just go and search for a definition, and you’ll see what I mean. However, from the broader technological perspective, time depends on how we measure it: it is what those measurements tell us. So, what if those measurements, even ones from the most accurate atomic clock sources around the planet, could be manipulated?
Welcome to the world of hacking time. Welcome to the world of Adam Laurie, the lead hardware hacker with the veteran hacking team that is IBM X-Force Red. It’s worth remembering at this point that hacking is not a crime, and this story serves well to illustrate the fact.
Full Story:

Researchers at ETH Zurich have discovered major vulnerabilities in DRAM memory devices, which are widely used in computers, tablets and smartphones. The vulnerabilities have now been published together with the National Cyber Security Centre, which for the first time has assigned an identification number for it.
When browsing the internet on a laptop computer or writing messages on a smartphone, we all like to think that we are reasonably safe from hacker attacks as long as we have installed the latest software updates and anti-virus software. But what if the problem lies not with the software, but with the hardware? A team of researchers led by Kaveh Razavi at ETH Zurich, together with colleagues at the Vrije Universiteit Amsterdam and Qualcomm Technologies, have recently discovered fundamental vulnerabilities affecting the memory component called DRAM at the heart of all modern computer systems.
The results of their research have now been accepted for publication at a flagship IT security conference, and the Swiss National Cyber Security Centre (NCSC) has issued a Common Vulnerabilities and Exposures (CVE) number. This is the first time that a CVE identification has been issued by the NCSC in Switzerland (see box below). On a scale of 0 to 10, the severity of the vulnerability has been rated as 9.

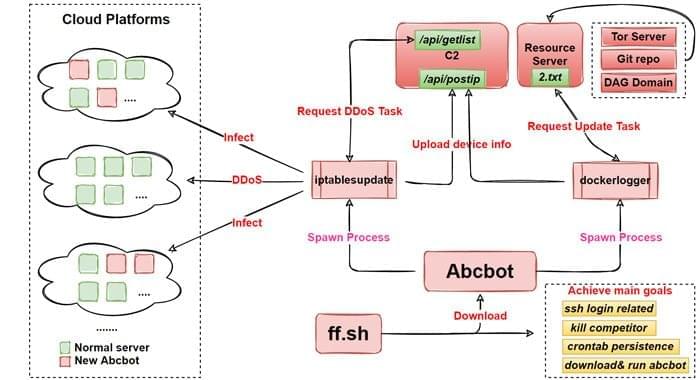
The notorious Emotet malware is staging a comeback of sorts nearly 10 months after a coordinated law enforcement operation dismantled its command-and-control infrastructure in late January 2021.
According to a new report from security researcher Luca Ebach, the infamous TrickBot malware is being used as an entry point to distribute what appears to be a new version of Emotet on systems previously infected by the former. The latest variant takes the form of a DLL file, with the first occurrence of the deployment being detected on November 14.
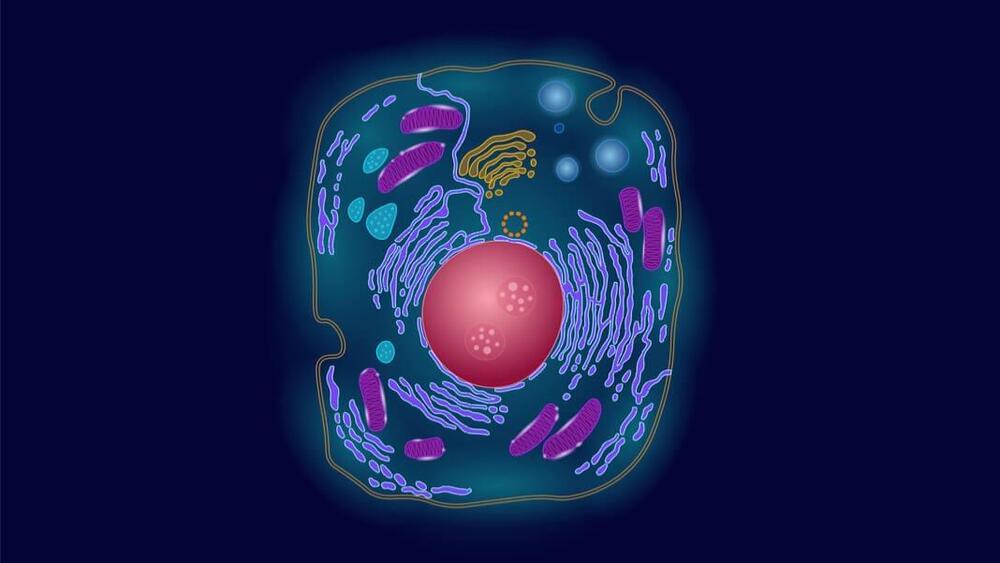
And it can be hacked.
The authors of a new study in Nature Catalysis reprogrammed these blobs—called exosomes—into an army of living nanobioreactors. It’s a seemingly simple process of mix and match: each blob is filled with a different chemical that’s involved in a biological reaction. By bringing two together, the blobs merge into a single squishy container, allowing the two chemicals to react.
The results were explosive. The tiny bioreactors pumped out energy molecules, called ATP, inside living cells. The burst of energy saved injured cells, providing them with a boost of power to fight back against dangerous molecules that otherwise lead to cell death.

The TechCrunch Global Affairs Project examines the increasingly intertwined relationship between the tech sector and global politics.
Criminals have a long history of conducting cyber espionage on China’s behalf. Protected from prosecution by their affiliation with China’s Ministry of State Security (MSS), criminals turned government hackers conduct many of China’s espionage operations. Alarming as it may sound, this is not a new phenomenon. An indictment issued by the U.S. Department of Justice last year, for example, indicated that the simultaneous criminal-espionage activity of two Chinese hackers went back as far as 2009. In another case, FireEye, a cybersecurity company, alleges that APT41, a separate cohort of MSS hackers, began as a criminal outfit in 2012 and transitioned to concurrently conducting state espionage from 2014 onward. But there’s reason to believe that since then, China has been laying the groundwork for change.
A spate of policies beginning in 2015 put China in a position to replace contracted criminals with new blood from universities. The CCP’s first effort in 2015 was to standardize university cybersecurity degrees by taking inspiration from the United States’ National Initiative for Cybersecurity Education — a NIST framework for improving the U.S. talent pipeline. One year later, China announced the construction of a new National Cybersecurity Talent and Innovation Base in Wuhan. Including all of the Base’s components, it is capable of training and certifying 70,000 people a year in cybersecurity.