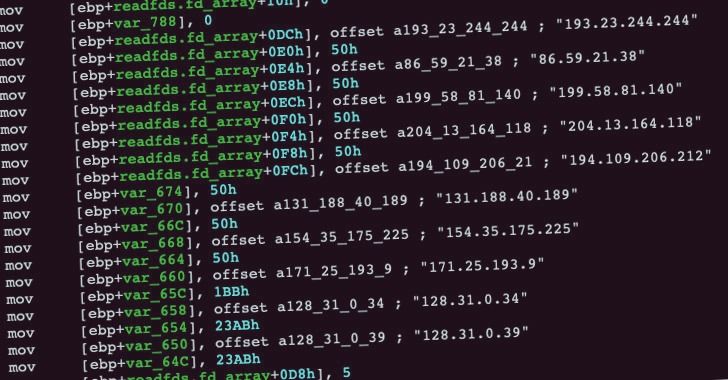
As the U.S. government works to contain a sprawling hacking campaign that relies on software in technology from SolarWinds, a federal contractor, technology firms are disabling some of the hackers’ key infrastructure.
Cybersecurity giant FireEye on Wednesday said that it had worked with Microsoft and the domain registrar GoDaddy to take over one of the domains that attackers had used to send malicious code to victim machines. The move is no panacea for stopping the suspected state-sponsored hacking campaign, though it could help stem the tide of victims, which reportedly includes the departments of Treasury and Homeland Security.
The seized domain, known as a “killswitch,” will “affect new and previous” infections of the malicious code coming from that particular domain, FireEye said in a statement that was first reported by independent journalist Brian Krebs. “Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution.”