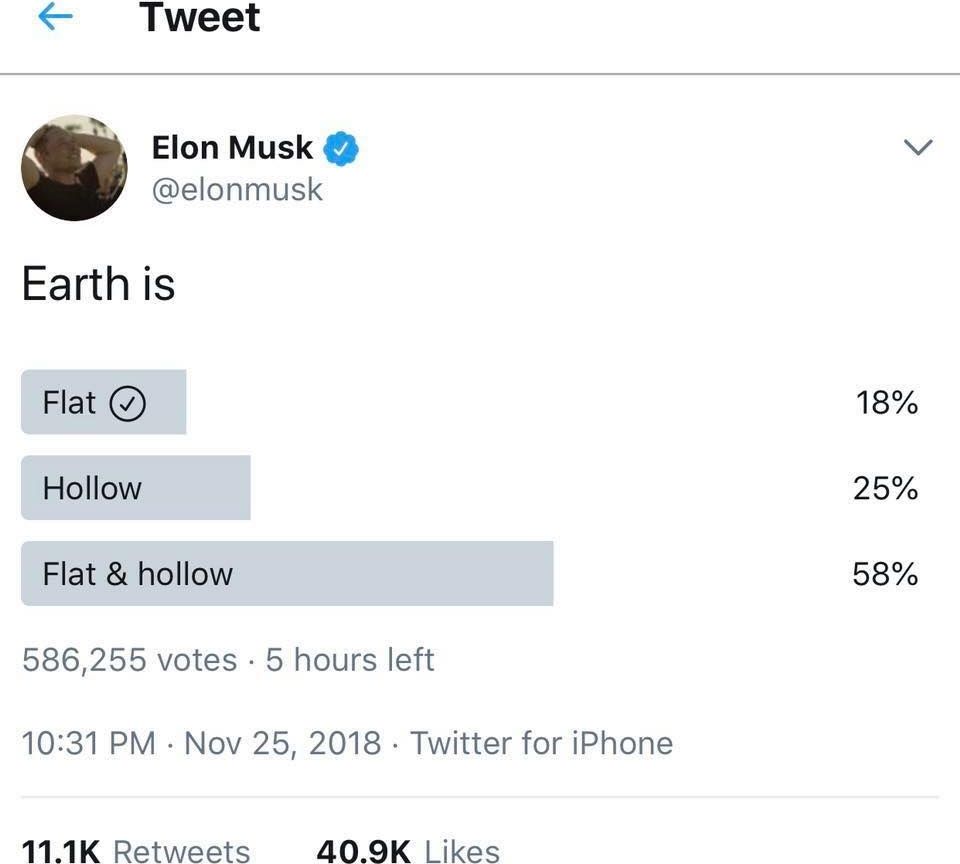
Looking forward to exploring my new home. go.nasa.gov/InSightRaws #MarsLanding




That’s why freedom of movement is one of the key conditions necessary to successfully share resources. Other necessary conditions include low population densities, low market value of the resources, variability in resource distribution and an ethos of sharing.
Sometimes, there is no “tragedy” in the tragedy of the commons, according to a new analysis that challenges a widely accepted theory.
Scientists have long believed that when there is open access to a shared resource, people will inevitably overuse it, leading to ruin for everyone—an idea known as the “tragedy of the commons.”
But in an analysis of eight case studies from around the world—from foragers in Australia to mangrove fishers in Ecuador—researchers found that people can successfully share and sustainably use resources, under certain conditions.

Also included in the dispatch: this snapshot from the lander’s arm showing the instruments in their new “plain perfect” home. Get the latest: https://go.nasa.gov/2FDGbwu
If you’re paranoid about your cyber security, you may not be so crazy after all.
The cybersecurity industry is experiencing a growth that is almost unparalleled across any other industry even taking into account historical figures. Some people say that the growth in the need of cybersecurity is going to create the biggest wealth transfer we have seen in our lifetime.
With every aspect of our life being fine-tuned with the use of data, making sure that data is secure is becoming a top priority around the globe. This is being reflected in the massive growth of the cybersecurity industry and the massive demand for individuals who have been trained to keep data safe.
Cybersecurity is the fastest growing technology sector out there. And with cybercrime at an all-time high, the cybersecurity niche is set for massive growth over the next 5 years.
The amount of money that individuals and businesses spend on cybersecurity is growing and is expected to be over $1 trillion cumulatively over the next five years, from 2017 to 2021.
Cybercrime and security breaches are continuing to cost businesses and individuals more and more money. The amount of damage done is expected to be $6 trillion annually by 2021, up from $3 trillion in 2015 according to Robert Herjavec, the founder and CEO of Herjavec Group, a Managed Security Services Provider.
There is an expectation that there will be 1.5 million cybersecurity job openings by 2019, a huge increase from just 1 million in 2016. By 2019, the demand is expected to increase to somewhere around 6 million globally according to Cybersecurity Ventures.
If you’re looking for a great career, recent studies suggest that cybersecurity unemployment rate will remain at 0% over the next 5 years, from 2017 to 2021.
The major reason cybersecurity is growing at such a rapid pace is the growth of cybercrime and the number of digital devices we use in our day to day life.
The rise of the Internet Of Things (or IoT for short) has provided hackers and malicious actors more opportunities to cause havoc than ever. And that havoc comes with real work $-signs attached to it. In fact, the number of IoT devices jumped by 31% to 8.4 billion in 2017 according to a Gartner study.
That means that there are more IoT connected devices than people on the plant, and with a great deal of those IoT devices being used for commercial applications in fields like Healthcare, security is truly becoming more and more important all the time.
According to IBM, the average loss experience by businesses who are victims of cybercrime is almost 4 million dollars. As businesses rely more and more on technical tools and software to complete day-to-day operations, they become more and more susceptible to cybercrime. What’s more is that the technology and tools are constantly changing at a pace that is faster than most businesses or individuals or able to keep up with.
In many cases, organizations are reluctant to uncover hacks and cyberattacks that they’ve been victims of, basically this behavior is inspired by a paranoid fear of reputation harm. All things considered, Cybersecurity Ventures is foreseeing somewhat higher development rates, at around 12 to 15 percent year-over-year through 2021.
To be put more simply, that estimate is higher than the 8–10% being anticipated by other industry analysts. Accordingly, the real spending on cybersecurity might be significantly more than what’s uncovered through studies & surveys, as organizations might downplay their cybersecurity spending plans with the end goal to secure shield whatever reputation harm it may cause.
Some organizations such as Bank of America have literally an unlimited cybersecurity budget. While this may seem weird, it’s also the fast approaching “new-norm” for large enterprise organizations. Where does that money go? The firms and companies that specialize in cybersecurity operations, management, and audits.
Other research from Morgan Stanley (overview from Chief Information Officers of real companies) reveals that the greater part of the officials they asked intended to purchase in excess of 15 diverse security products in the next year, demonstrating the tremendous layers of security that are attempted in numerous enterprise environments and further featuring the huge increase in spending on cybersecurity services & audits.
This tells us that, as cybercrime costs keep on going up for companies, by and large so will spending for cybersecurity measures, thus creating a boon for the cybersecurity business.
And if you’re not a business, the possible downsides to a hack can be harder to get over. With the actual possibility of having your life ruined, individuals are starting to explore more options to maintain online anonymity and privacy.
Beside the developing number of direct & focused assaults that is driving the profitability in cybersecurity, the quantity of cybersecurity venture capital deals likewise are developing in this space. There has been a huge increase in the amount of funding firms have received, about $13.6 billion has been invested into cybersecurity organizations since 2013.
Not only is hacking and malicious behavior driving industry growth, but compliance regulations also. With regional changes like GDPR compliance, businesses are under even more pressure to contract or retain cybersecurity services.
This pressure doesn’t only extend to hiring trained professionals to implement the compliance requirements, but businesses also have to worry about fines and charges associated with not keep up with and following current regulations.
“If GDPR were an asteroid hurtling towards the United States, those directly in the strike zone would be large, multinational companies,” said Heather Engel, the CSO at Sera-Brynn, a global cybersecurity firm.
Hackers and malicious actors spend the entirety of their day finding new exploits in holes in currently used security tools methods and standards.
If you are a consumer who doesn’t take security seriously or are a business not employing a cybersecurity professional to keep you safe, you may find yourself contributing to the tremendous growth the cybersecurity industry & cybersecurity professionals are experiencing. It’s obvious that “biggest growing market” may be the understatement of the century.

Here’s a 2-min video of my recent talk in #Dubai for the inaugural #GSTalksUAE event. I was really excited that the UAE Prime Minister’s Office brought me in to talk specifically on #transhumanism and how it might improve Government Services. In the last year, many countries around the world have been getting in touch with me to better understand transhumanism and our changing #future. Click on the link to watch the video: https://www.instagram.com/p/BqcN2bUHnwA/?utm_source=ig_share_sheet&igshid=nrrshfl4a94i&fbclid=IwAR0JoxB2sHoTcgiN4-T-tBSnhcUkZjfCZuqEBQTY-hyQWRYgMCusMlfQd4g&h=AT1WzKbkeE5T0jOd6PxzuHWVG0kP_i0Ib3ODFRxfolqjRyJ8IsnVU1TsdfVnjDPNciDybgqtrTnkdW2v8dxz6skubry8gxI3KKrnRzRF3AJyc8Uwjahwk5tNnmr20bwfWU5onAVwXQb3OfRFfnnO0K_KXMga9IE5_ASuEA

